Enforcing Passwordless Logins with AADJ Windows 10 and Endpoint Manager Intune (Part 2)
Enforcing Passwordless Logins with AADJ Windows 10 and Endpoint Manager (Intune) In the last blog post, we enabled FIDO2 security key logins with...
As companies like Yubico announce the next generation of YubiKeys with biometrics, let’s take a look at what is actually possible today with Azure AD Joined Windows 10 devices. Microsoft pushes us closer and closer to passwordless login options, but without a domain and GPOs available, some of our clients are left wanting. In this series of blog posts, I am going to walk through the setup of a FIDO2 device in Azure AD and Windows 10, and later apply Intune policies to alter login options.
Few notes before you get started:
Open the Azure AD Portal, and browse to Authentication methods:
https://portal.azure.com/#blade/Microsoft_AAD_IAM/AuthenticationMethodsMenuBlade/AdminAuthMethods
To pilot this, I am just going to enable a single user. Choose FIDO2 Security Key, then click Enable, select your user or group of pilot users and finally click Save.
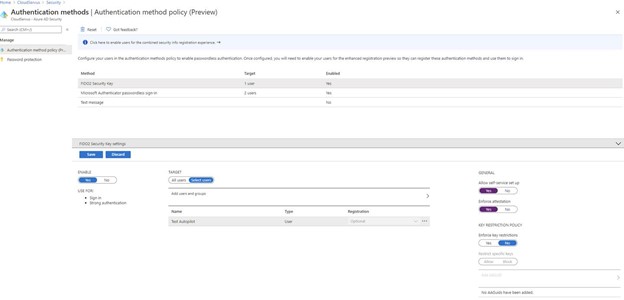
This user or group of users will now be able to setup a security key, in this example I will be using a YubiKey 5 on a Windows 10 device that is Azure AD Joined.
On your Windows 10 machine, open Edge and browse to: https://myprofile.microsoft.com/
Click UPDATE INFO under Security Info.
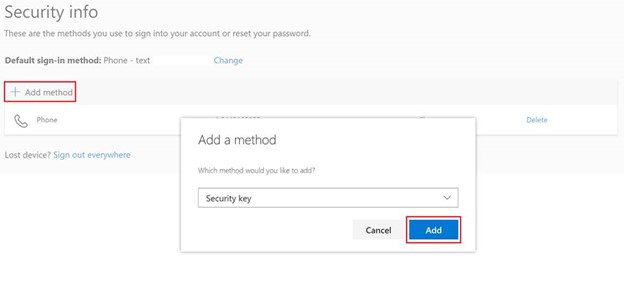
Click Add method, then choose Security Key. You will be prompted for MFA.
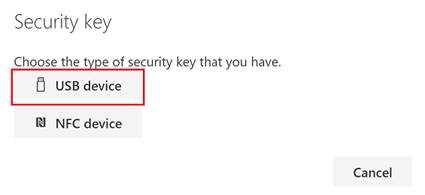
In this case, I am setting up a USB C YubiKey 5, so selecting USB Device at the prompt.
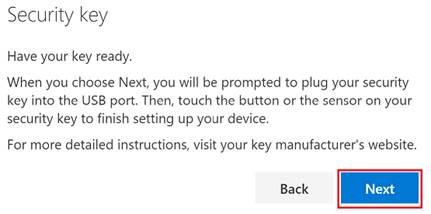
Insert your device, then click Next.
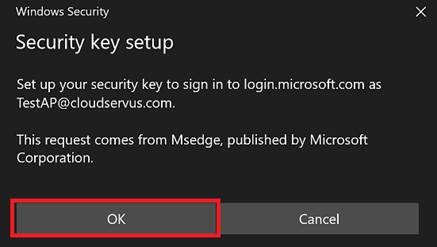
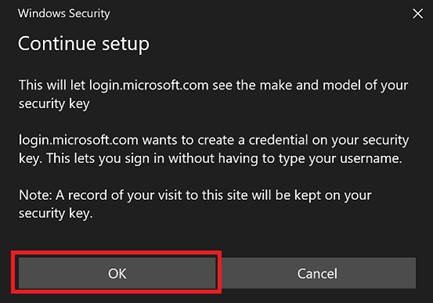
Click OK at the prompts to add your sign-in to the YubiKey, then create a PIN.
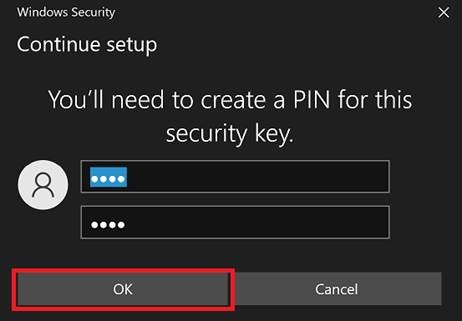
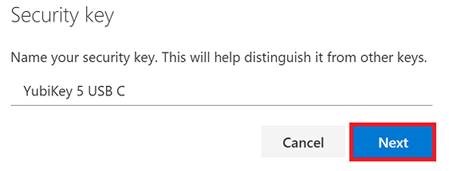
All that is left is to give your key a name in Azure AD. You can have multiple keys, so being able to tell them apart is important.
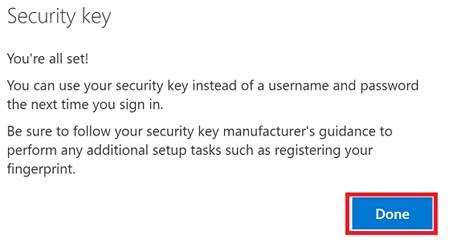
Finished!
All that is left to do is test the login on our Windows 10 machine, so at the Lock Screen there is now an option for Windows password, FIDO security key, or Windows Hello for Business PIN.
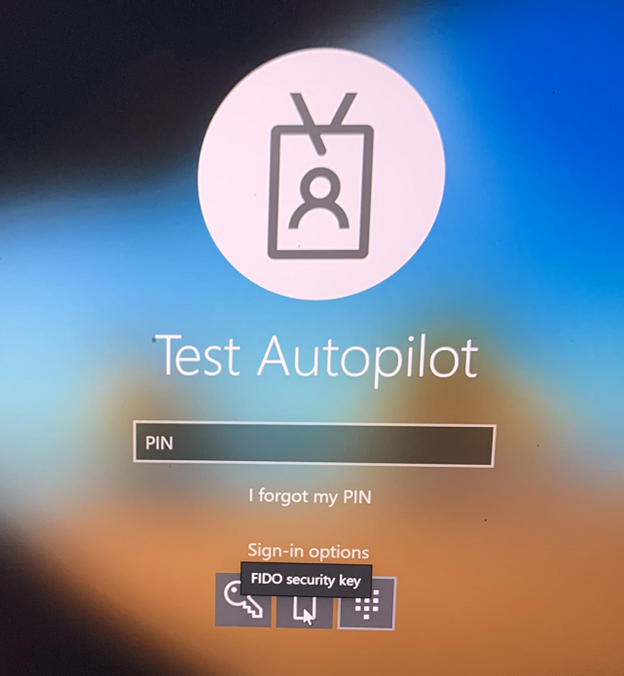
Click Sign-in options, then FIDO security key.
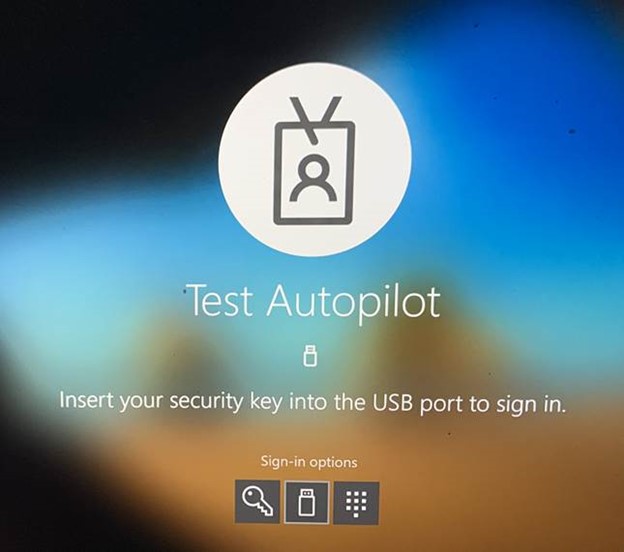
Insert your security key and you will be prompted for the key’s PIN (not a Windows Hello for Business PIN).
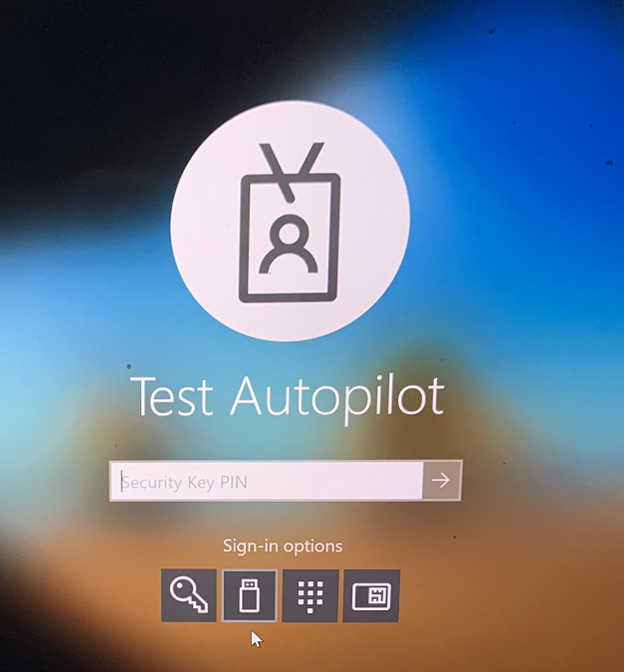
YubiKeys have a physical button to touch, so once the correct PIN is entered, all that is left to do is touch the key and login is successful without a password!
What does this look like in Azure AD? It will show as a multi-factor login with FIDO2 security key:
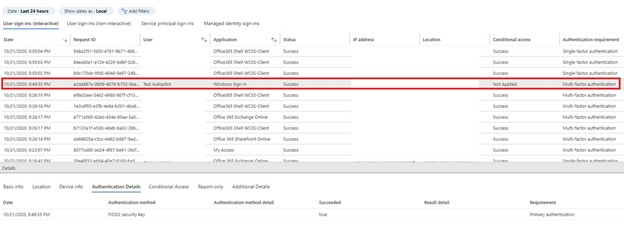
The option is still available for username and password login to Windows 10, so what is possible with Intune policies to try to enforce a smart card type login? We will look at those in the next post…
Blog Post Written By: Nick Krenek (Principal M365 Security Consultant at CloudServus)

Enforcing Passwordless Logins with AADJ Windows 10 and Endpoint Manager (Intune) In the last blog post, we enabled FIDO2 security key logins with...
Full Azure AD P1 is coming to M365 Premium ⚡ For our customers under 300 employees, Azure Active Directory Plan 1 is coming to M365 Business...

Recently, CloudServus received a high-severity alert from the Microsoft 365 Security & Compliance Center of one of our clients: a user account had...